Cybersecurity Firm Maintains FedRamp Authorization with Containers
- août 23, 2022
According to a 2021 CNCF survey on containers and Kubernetes, 93% of respondents are currently using, or planning to use containers in production, while 58% used containers in the last month. From 2020 to 2021, there was a 49% year-on-year increase in overall container adoption. We expect to see this type of rapid adoption to accelerate as containers become the preferred way to package and implement applications on Kubernetes clusters.
But deploying containers may expose complexity, cultural and security challenges that need to be fully understood, especially for companies that work with the US federal government. So being experts in both containers and FedRAMP, we helped a large cybersecurity consulting and managed services firm establish a way to deploy containers within FedRamp requirements, as the company looked to improve its security posture and better serve its US Federal clients.
FedRamp and Containerized Applications
FedRamp (Federal Risk and Authorization Management Program) is a US federal government program that delivers a standard approach for security assessment, authorization, and continuous monitoring. Companies that serve the US federal government should have their services FedRamp authorized and compliant. According to FedRamp, the following high-level requirements must be addressed to systems running containerized applications (FedRamp’s vulnerability scanning requirements for containers can be found here):
- Hardened images – Container images should be hardened in accordance to the relevant benchmarks
- Container orchestration pipeline – The provider must leverage an automated container orchestration tool to build, test and deploy containers to production.
- Vulnerability scanning for container images – Images should be scanned for vulnerabilities at build, deploy and runtime. Any live container should be scanned at least every 30 days.
- Security sensors – Security sensors should be deployed to inventory and monitor containers
- Registry monitoring – The container registry should be monitored and scanned for vulnerabilities
- Asset management and inventory reporting – Running containers should be uniquely tracked and reported through an automated mechanism.
Implementation for a Cybersecurity Client
For this project, our client wanted to ensure it remained FedRAMP authorized and use containers to help it detect and respond faster to digital risks. Once we understood the requirements and designed the best container solution, we sat down with the client and reviewed the implementation plan, which included:
- Hardening the pipeline using Bitbucket CD to build a hardened base container image according to CIS benchmarks (See Figure 1 below).
- Registry scanning to monitor and scan new images in the container registry (See Figure 2 below).
- Periodic scanning of all live containers.
- Reporting of vulnerabilities for container images during build, deployment and run-time.
- Implemented customized policy evaluation for FedRamp security compliance.
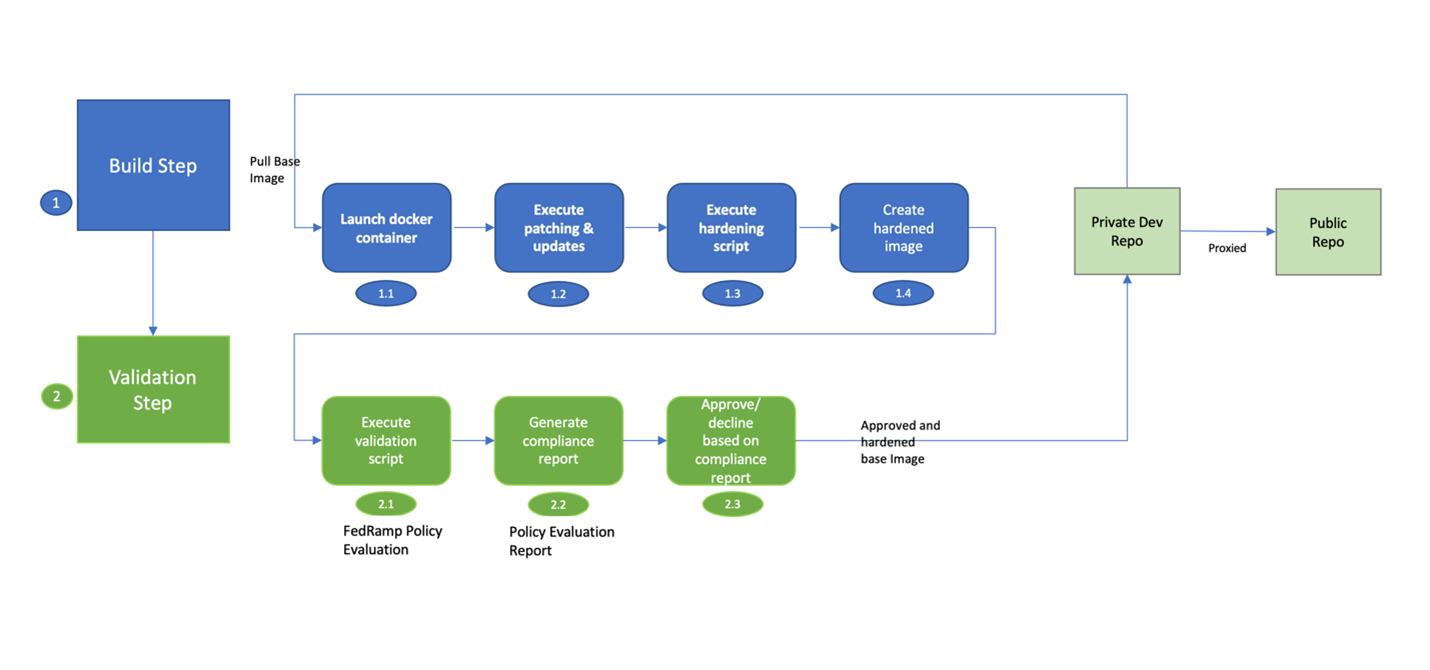
Figure 1: Container hardening pipeline
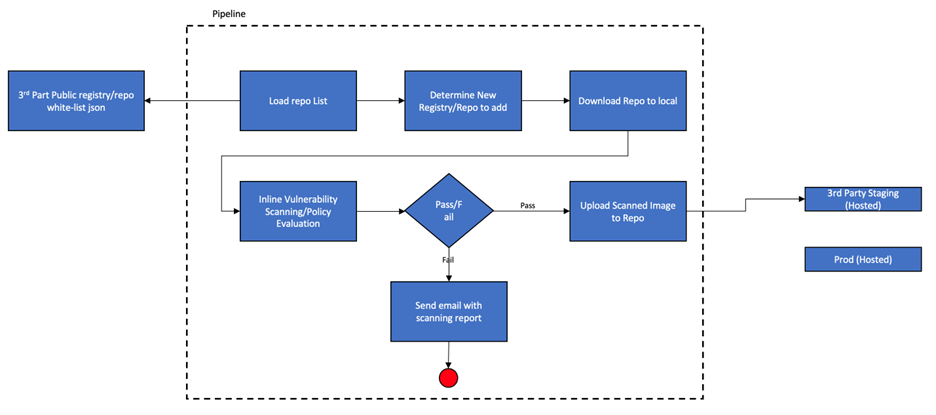
Figure 2: Vulnerability scanning for containers at build
Driving Better Outcomes
Our client was excited to deploy containers in production, serve its clients better, and improve its overall security posture through the proper implementation of a container solution that kept the client FedRAMP authorized. If you’re thinking about using containers, be sure to check out some of our other blog posts on the topic:
- Shorten the AWS Container Journey
- Build a Strong Foundation Before Migrating Applications to AWS
- Application Replatforming for the Cloud in Six Steps
- Why We Expect AWS Bottlerocket to Take Off
Subscribe to our blog




