Docker Tutorial Series, Part 5: Docker Security
- May 28, 2014
Security is taken seriously when dealing with open source accountability. And it’s no different when developers embrace using Docker, by building applications locally right up to production deployments. A big responsibility that comes with being deployed in so many places is a serious focus on the security of Docker as a project and a platform.
Docker Security
As a result, we’ve decided to discuss in part 5 of our Docker Tutorial Series, the key areas of security Docker focuses on and why they matter to overall Docker Security. Given that Docker is typically an extension of LXCs, it easily uses the security features of LXCs, too.
In the first part of this series, we discussed that a docker run command is executed to spin up and run a container. However, here’s what really happens:
- A docker run command is initiated.
- Docker runs lxc-start to execute the run command.
- A set of namespaces and control groups are created for the container by lxc-start.
For those who are not aware of the namespace and control group concepts, namespace is the first level of isolation whereas no two containers can view or control the processes running in each of them. Each container is assigned a separate network stack, and, hence, one container does not get access to the sockets of another container. To allow IP traffic between the containers, you must specify public IP ports for the container.
Control Groups, the key component, has the following functionalities:
It is responsible for resource accounting and limiting.
Provides metrics pertaining to the CPU, memory, I/O and network.
Tries to avoid certain DoS attacks.
Has significance on multi-tenant platforms.
Docker Daemon’s Attack Surface
Docker daemon runs with root privileges, which implies there are some issues that need extra care. Some interesting points include the following:
Control of Docker daemon should only be given to authorized users as Docker allows directory sharing with a guest container without limiting access rights.
The REST API endpoint now supports UNIX sockets, thereby preventing cross-site-scripting attacks.
REST API can be exposed over HTTP using appropriate trusted networks and VPNs.
Run Docker exclusively on a server (when done), isolating all other services.
Some key Docker security features include the following:
Processes, when run as non-privileged users in the containers, maintain a good level of security.
Apparmor, SELinux, GRSEC solutions can be used for an extra layer of security.
There’s a capability to inherit security features from other containerization systems.
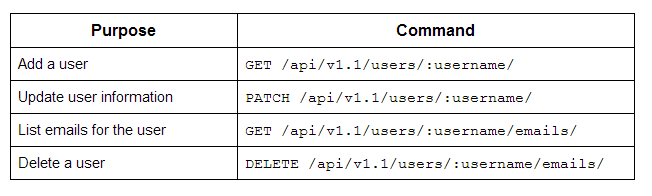
Docker.io API
For managing several processes relating to authorization and security, Docker provides a REST API. The following table lists some commands pertaining to this API for maintaining functions related to security.
Did you find this useful?
Interested in getting tips, best practices and commentary delivered regularly? Click the button below to sign up for our blog and set your topic and frequency preferences.
Subscribe to our blog




